Don't believe the hype: That GRUB backspace bug wasn't a big deal

 Image: Sunny Ripert
Image: Sunny RipertYou can hack any Linux system just by pressing the backspace key 28 times! That’s what some sites would have you believe after an unfortunate GRUB bug was recently made public. But this won’t actually allow you to easily own any Linux system.
You should still update GRUB
Obviously, this isn’t ideal. This bug will only impact some of the most secured systems. If you use GRUB’s password feature to lock down your bootloader, you’ll want to install the security updates your Linux distribution provides. The big Linux distributions have patched this problem, so it’s simply a matter of installing those security patches, like you should be doing on a regular basis anyway. You don’t even need to reboot. The next time your computer boots, it’ll use the new version of GRUB without the bug and be secure.
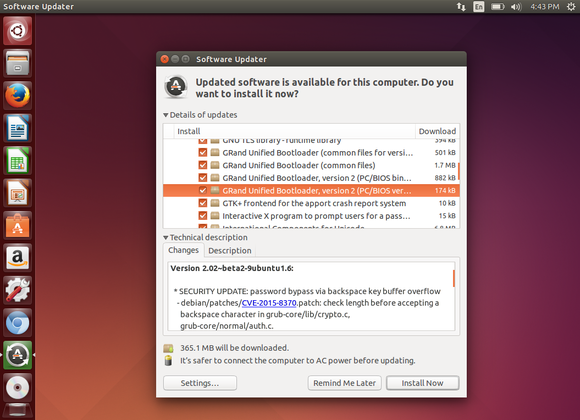
Security updates for GRUB are available from your Linux distribution.
GRUB normally doesn’t even use a password
That said, this bug won’t allow you to hack any Linux system. The average Linux user doesn’t need to worry about it. Here’s why:
Most Linux systems don’t have a GRUB password at all. By default, Linux distributions don’t set up any GRUB password. Just rebooting the computer and reaching a GRUB shell will give you full access to boot the kernel with any parameters you want. You could then gain administrator access and replace system files with malicious ones, just as these researchers did. The majority of Linux systems out there are vulnerable to this. A GRUB password isn’t the same thing as a login password. In fact, there’s no way to set a password for the Windows bootloader at all.
But thats okay, because this attack requires physical access to the computer. You can’t access GRUB over a network connection. If an attacker has physical access to a computer and can reboot it and use a keyboard and mouse, that computer is already in trouble. At a minimum, if it’s a server, an attacker can cause a denial-of-service attack by physically shutting down the computer or unplugging its network cable. The attacker could also open up the computer, remove the hard drive, mess with the files on it, and then put that compromised hard drive back in the computer. The attacker could install a key-logging device between the keyboard and computer, for example. Or, the attacker could boot an operating system from a USB drive and use it to mess with the computers files. The sky’s the limit with physical access.
You can normally edit boot parameters in grub by pressing “e,” no password required!
What’s more, none of this really matters if you use disk encryption. If your files are encrypted and you have to enter a password to access them, an attacker wouldn’t be able to use the GRUB bug to access your files and compromise them. An attacker also wouldn’t be able to use the usual passwordless GRUB prompt to mess with your files.
So, in the very rare case where an attacker has physical access to a locked-down Linux system—including a keyboard and mouse—but not physical access to the computer’s case, this bug could matter. There may be some systems like that out there, but not many. The vast majority of Linux users aren’t using a GRUB password and don’t need to. They were never affected by this bug at all.
Linux security isn’t perfect. ShellShock was particularly horrific, for example. But this GRUB bug isn’t anywhere near as bad. Like that XOR malware, it doesn’t affect most Linux users.






