Security bugs in popular phone-tracking app iSharing exposed users' precise locations
![]()
Last week when a security researcher said he could easily obtain the precise location from any one of the millions of users of a widely used phone-tracking app, we had to see it for ourselves.
Eric Daigle, a computer science and economics student at the University of British Columbia in Vancouver, found the vulnerabilities in the tracking app iSharing as part of an investigation into the security of location-tracking apps. iSharing is one of the more popular location-tracking apps, claiming more than 35 million users to date.
Daigle said the bugs allowed anyone using the app to access anyone else’s coordinates, even if the user wasn’t actively sharing their location data with anybody else. The bugs also exposed the user’s name, profile photo and the email address and phone number used to log in to the app.
The bugs meant that iSharing’s servers were not properly checking that app users were only allowed to access their location data or someone else’s location data shared with them.
Location-tracking apps — including stealthy “stalkerware” apps — have a history of security mishaps that risk leaking or exposing users’ precise location.
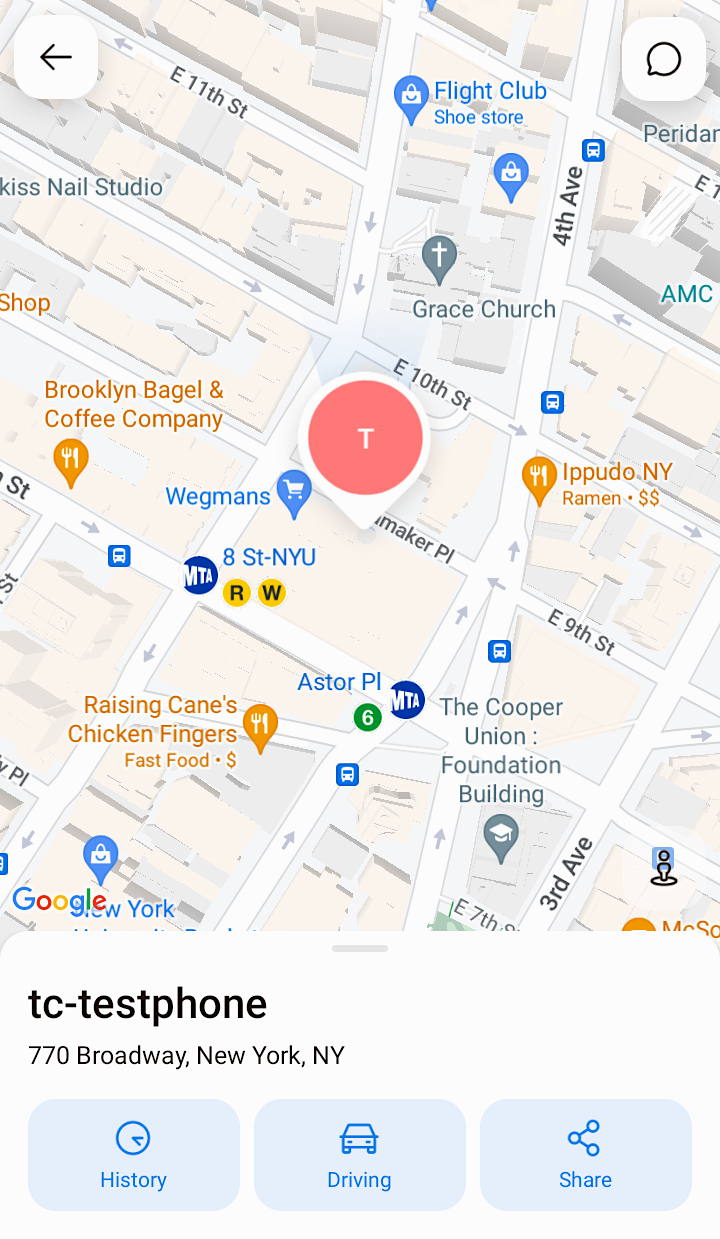
In this case, it took Daigle only a few seconds to locate this reporter down to a few feet. Using an Android phone with the iSharing app installed and a new user account, we asked the researcher if he could pull our precise location using the bugs.
“770 Broadway in Manhattan?” Daigle responded, along with the precise coordinates of TechCrunch’s office in New York from where the phone was pinging out its location.
Daigle shared details of the vulnerability with iSharing some two weeks earlier but had not heard anything back. That’s when Daigle asked TechCrunch for help in contacting the app makers. iSharing fixed the bugs soon after or during the weekend of April 20-21.
“We are grateful to the researcher for discovering this issue so we could get ahead of it,” iSharing co-founder Yongjae Chuh told TechCrunch in an email. “Our team is currently planning on working with security professionals to add any necessary security measures to make sure every user’s data is protected.”
iSharing blamed the vulnerability on a feature it calls groups, which allows users to share their location with other users. Chuh told TechCrunch that the company’s logs showed there was no evidence that the bugs were found prior to Daigle’s discovery. Chuh conceded that there “may have been oversight on our end,” because its servers were failing to check if users were allowed to join a group of other users.
TechCrunch held the publication of this story until Daigle confirmed the fix.
“Finding the initial flaw in total was probably an hour or so from opening the app, figuring out the form of the requests, and seeing that creating a group on another user and joining it worked,” Daigle told TechCrunch.
From there, he spent a few more hours building a proof-of-concept script to demonstrate the security bug.
Daigle, who described the vulnerabilities in more detail on his blog, said he plans to continue research in the stalkerware and location-tracking area.
Read more on TechCrunch:
A family tracking app was leaking real-time location dataInside TheTruthSpy, the stalkerware network spying on thousandsYour Android phone could have stalkerware — here’s how to remove itTechCrunch launches TheTruthSpy spyware lookup tool‘Reverse’ searches: The sneaky ways police tap tech giants for your private data
To contact this reporter, get in touch on Signal and WhatsApp at +1 646-755-8849, or by email. You can also send files and documents via SecureDrop.






